Public Keys
Public Key Encryption
The the methods so far all have a basic weakness: the encryption method or key needs to be kept secret. But keeping the key private is almost as hard as keeping the message private. In 1976 Ron Rivest, Adi Shamir, and Len Adleman devised an ingenious method (now known as RSA) that allows a person to announce publicly how anyone can encode a message to him so that only he is able to decipher it. The information, which is given away to everybody, is called the public key. The information which is needed for deciphering (the private key) is known only by the person for whom the message is intended. If Bob wants to send Alice a secret message, he enciphers it with Alice's public key. Then no one else can decipher it, even knowing her public key. Only her private key can undo the encryption, and you can't figure out the private key from the public key.
- It may seem incredible that Alice can make her encryption key public and still no one except her can decrypt her message. The RSA method relies on some mathematics and on some limitations on the speed of current computers. Read "Secrecy Changes Forever" (Blown to Bits pages 178-181) to understand some of how this works.
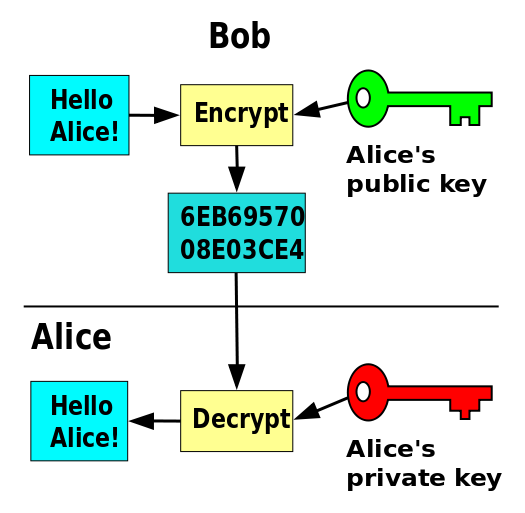
Here is a model of public key encryption (from wikimedia.org)
- With a partner, discuss how this picture is different from the one on the previous page. Would you trust this method to work to send your own credit card number?
- Read "The Key Agreement Protocol" and "Public Keys for Private Messages" (Blown to Bits pages 181-183) for more details on Public Key Encryption.