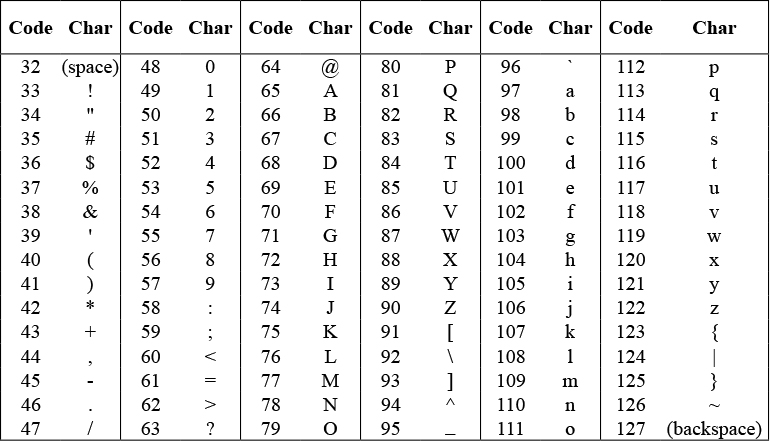
Computers store keyboard characters (capital and small letters, punctuation marks, space, digits, symbols, and so on) as numbers called Unicode. This table shows the Unicode for some of the keyboard characters:

The unicode of block reports the number that is used for a particular character:

The unicode as letter block reports the character that a given Unicode number represents:
unicode of and unicode as letter blocks. Try changing a word into Unicode, telling the Unicode to a friend, and then having them change it back into a word.Why do we see characters like = ? @ # ^ * { or ~ ?
You can safely assume that shifting any set of text characters a reasonable distance will result in a set of printable characters, which may include non-alphanumeric (not letter or digit) characters.
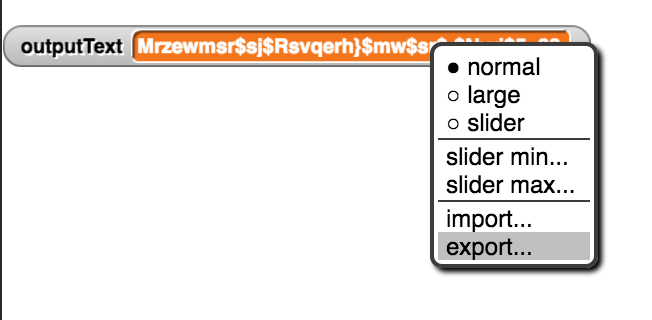
For example, if we use a shift of 4 to encrypt:
Invasion of Normandy is on 6 June 1944
it becomes:
Mrzewmsr$sj$Rsvqerh}$mw$sr$:$Nyri$5=88
What if your decrypted text is missing some letters?
If you copy your encrypted message with a method other than by using copy and paste (for example, by writing it by hand or typing it into a phone), some characters may disappear from your message. This is because some of the Unicode characters after 126 are printing characters that symbolize things like "delete." These characters won't get displayed in Snap!, so you can't copy them by hand, but if you use copy and paste, Snap! knows they are there. In Take It Further exercise A, you can develop a method of encryption that avoids this problem.
initials block from your U3L2-ContactList project so that it will find the initials for a person with a hyphenated name like Alexandria Ocasio-Cortez.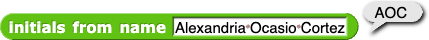
map, keep, and combine on Unit 3 Lab 2 Page 5: Transforming Every List Item.)
unicode block to select all the capital letters rather than splitting by word breaks.
is between? from your U2L4-MathLibrary project to check which Unicode values are capital letters. (You learned about exporting and importing blocks on Unit 2 Lab 4 Page 2: Making a Mathematical Library.)split block to check for hyphens as well as to check for spaces between words.
split, note that the second input to split can be the character you want to use as the word separator. (You learned about split on Unit 3 Lab 2 Page 5: Transforming Every List Item.)